Wednesday, May 21, 2025
Monday, May 5, 2025
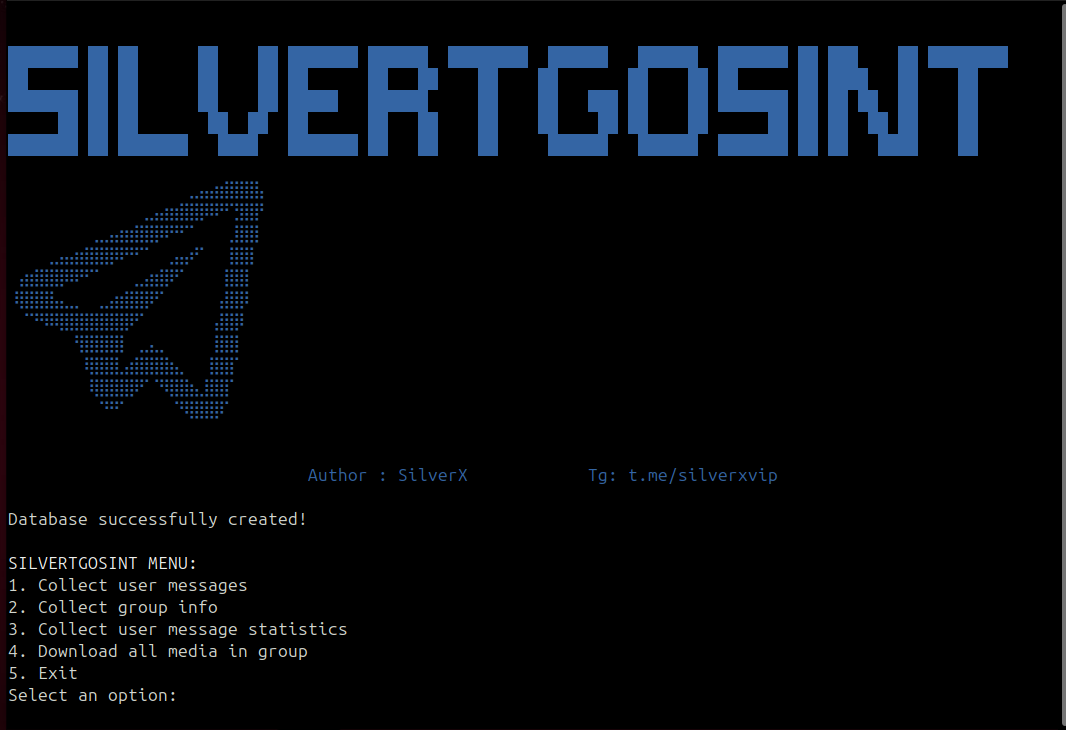
This tool connects to your Telegram account using the API ID and API hash and retrieves all messages of the target user from the groups you are in, saving them to a TXT file and additionally storing them in a database.
When logging in, you need to access your Telegram account via my.telegram.org and generate an API ID and API hash.
Additionally, if the target group is publicly accessible, various details such as ID, username, name, number, etc., can be collected.
Useful Note: You can add the account linked to this tool to hundreds of groups and collect the target’s messages from all those groups.
- All groups the target user is in and all messages they have sent in those groups are collected.
- Statistics on how many messages the target has sent in each group are gathered (this allows you to see which group they are most active in).
- All members of the target group (in ID, name, username, and number format) are collected and saved to a TXT file.
- All media from the target group is downloaded.
- Obtain API credentials from my.telegram.org:
- Login and navigate to "API development tools."
- Create a new app and note the
API IDandAPI Hash.
- Clone this repository:
git clone https://github.com/silverxpymaster/silvertgosint.git - Navigate into the project folder:
cd silvertgosint - Download the required libraries
pip install -r requirements.txt - Run the tool:
python silvertgosint.py
- This tool requires authentication with Telegram using a phone number and an active session.
- The SQLite database stores collected messages for further analysis.
SilverInstaEye is a comprehensive OSINT tool for Instagram. It gathers extensive information about the target user. Support my GitHub repo by giving it a star! ⭐
- Basic information - Number and email (masked format), ID, username, number of posts, bio, number of followers, whether the account is private or public, whether it is a business account, etc..
- Download Posts: Bulk download all available posts from a target account.
- Collect Comments: Extract and store comments from posts.
- Retrieve Followers & Following Lists: Export lists of followers and the accounts being followed.
- Download Stories Anonymously: Downloading the target stories anonymously.
- Identify Posts with User Comments (Dorking): Extracting the posts that the target has commented on.
- Extract Geolocation from Posts: Retrieve and analyze geolocation data embedded in posts.
- Download Instagram Highlights: Save all highlight stories from a profile.- Clone the repository:
git clone https://github.com/silverxpymaster/SilverInstaEye.git cd SilverInstaEye - Install dependencies:
pip install -r requirements.txt - Run the tool:
python3 silverinstaeye.py
- The session is saved in
session.json. Make sure to keep this file secure. - Modify API request headers if necessary for stability and efficiency.
This tool is intended for educational and research purposes only. Unauthorized use of Instagram data may violate Instagram's policies. Use responsibly.
Sunday, December 1, 2024
Wednesday, September 18, 2024
Internet Download Manager (IDM) Full
Internet Download Manager is a device to develop download speeds by to numerous occasions, resume and timetable downloads. Complete error recovery and resume capacity will restart broken or interfered with downloads due to lost affiliations, compose issues, PC shutdowns, or unexpected power outages. Essential practical UI makes IDM straightforward and easy to use.
Internet Download Manager IDM
has a wise download method of reasoning reviving specialist that features shrewd interesting record division and safe multipart downloading development to stimulate your downloads. Not at all like other download executives and enlivening operators Internet Download Manager bits downloaded reports logically during the download process and reuses available relationships without additional interface and login stages to achieve the best-expanding pace execution.
Internet Download Manager IDMan
supports go-between servers, FTP and HTTP shows, firewalls, redirects, treats, endorsement, sound, and video substance getting ready. IDM facilitates impeccably into Microsoft Internet Explorer, Netscape, MSN Explorer, AOL, Opera, Mozilla, Mozilla Firefox, Mozilla Firebird, Avant Browser, MyIE2, and all other conspicuous projects to normally manage your downloads. You can in like manner move records, or use Internet Download Manager from the request line. Internet Download Manager can dial your modem at the set time, download the reports you need, by then hang up or even shut down your PC when it’s set.
Interpretation incorporates Windows 11 + 10 likeness, incorporates IDM download board for web-players. It furthermore features complete Windows 8.1 (Windows 8, Windows 7, and Vista) support, page grabber, redeveloped scheduler, and MMS show support. The new structure similarly incorporates an improved blend for IE 11 and IE-based projects, an updated and redesigned download engine, the exceptional moved coordination into each latest program, an improved toolbar, and a wealth of various upgrades and new incorporates.
Internet Download Manager (IDM) is a software tool that allows you to download files from the internet at high speeds. It can accelerate downloads by splitting the file being downloaded into smaller parts and downloading them simultaneously, which can significantly reduce the download time. IDM also has the ability to resume downloads if they are interrupted for any reason, such as a lost internet connection or a power outage. IDM is available for Windows operating systems, and it can be used to download a wide range of file types, including videos, music, documents, and more. It is a paid software, but you can try it for free for a limited time before purchasing a license.
Internet Download Manager (IDM) is a software program that allows you to download files from the Internet at a faster speed. It can download files using multiple connections to the server, which can increase the download speed significantly. IDM also has features such as pause and resume, which can be helpful when downloading large files. IDM is available for Windows and can be used to download files from a variety of websites, including video sites like YouTube. It is a paid software, but a trial version is available for users to try before purchasing.
To use Internet Download Manager (IDM), follow these steps:
- Download and install IDM on your computer.
- Open IDM and click on the “New Download” button.
- In the “New Download” window, enter the URL of the file you want to download and click “OK”.
- IDM will begin downloading the file. You can view the download progress in the main IDM window.
- Once the download is complete, the file will be saved to the location you specified in the IDM settings.
You can also use IDM to download files from a web page. To do this, follow these steps:
- Open the web page with the file you want to download.
- Click on the link to the file.
- IDM will automatically start downloading the file. If it does not, you can right-click on the link and select “Download with IDM” from the context menu.
IDM has many other features and options that you can use to customize your downloads, such as the ability to schedule downloads, set download priorities, and limit the download speed. You can access these options by clicking on the “Options” button in the IDM main window.
There are a few ways you can potentially make money from Internet Download Manager (IDM), a software tool that helps users download files from the internet more quickly and efficiently. Here are a few options to consider:
- Sell IDM as a standalone product: If you have a large audience or a platform where you can promote and sell software, you could potentially sell IDM as a standalone product. This could be done through an online store or through a platform like Amazon or eBay.
- Sell IDM as part of a bundle: Another option is to bundle IDM with other software products and sell the bundle as a package. For example, you could create a bundle of productivity tools that includes IDM and sell it to users who need a suite of tools to help them work more efficiently.
- Offer IDM as a paid upgrade: If you already have a popular software product or service, you could offer IDM as a paid upgrade or add-on. This could be a good way to generate additional revenue from your existing customer base.
- Offer IDM as a premium feature: If you have a freemium product or service, you could offer IDM as a premium feature that users can purchase to access additional functionality.
It’s important to note that if you plan to sell IDM, you will need to have the proper licenses and permissions to do so. You should also be aware of any applicable laws and regulations related to the sale of software products.
Internet Download Manager (IDM) is a popular software program designed to manage and accelerate downloads on Windows operating systems. It is developed by Tonec Inc. and is known for its ability to enhance download speeds, resume interrupted downloads, and organize downloaded files. Here are some key features and aspects of Internet Download Manager:
- Download Acceleration: IDM uses dynamic file segmentation and multi-part downloading technology to accelerate downloads. This helps to maximize download speeds by dividing files into smaller segments and downloading them simultaneously.
- Resume Capability: One of the notable features of IDM is its ability to resume interrupted or paused downloads. If a download is interrupted due to a lost connection, network issues, or other reasons, IDM can pick up from where it left off.
- Browser Integration: IDM integrates with popular web browsers such as Google Chrome, Mozilla Firefox, Microsoft Edge, and others. This allows users to initiate downloads directly from the browser and manage them through IDM.
- Scheduler: Users can schedule downloads at specific times, making it convenient to manage large downloads without the need for manual intervention.
- Batch Downloads: IDM supports batch downloads, enabling users to download multiple files simultaneously. This is useful for downloading large sets of files or entire web pages.
- Automatic Virus Checking: IDM has the ability to automatically check downloaded files for viruses using popular antivirus programs to ensure the safety of the downloaded content.
- Drag and Drop: Users can drag and drop URLs or files directly into IDM to initiate downloads, providing a quick and easy way to start downloading.
- Built-in Download Categories: IDM allows users to organize their downloads into various categories, making it easier to manage and locate specific files.
- Protocol Support: IDM supports various protocols, including HTTP, HTTPS, FTP, and others, making it versatile for downloading files from different sources.
- Customizable Interface: Users can customize the IDM interface according to their preferences, including themes and layout options.
It’s important to note that IDM is a paid software, but it offers a free trial period for users to evaluate its features. Keep in mind that using IDM to download copyrighted material without proper authorization may violate copyright laws in some jurisdictions. Always ensure that you have the right to download and distribute any content.
If you are experiencing issues with Internet Download Manager (IDM), there are a few things you can try to troubleshoot and fix the problem:
- Restart IDM and your computer: Sometimes, simply restarting IDM and your computer can help resolve any issues you are experiencing.
- Check your internet connection: Make sure that your internet connection is stable and working properly. If you are experiencing issues with your internet connection, it could be affecting your ability to download files with IDM.
- Check for updates: Make sure you have the latest version of IDM installed. IDM frequently releases updates to fix bugs and improve performance, so updating to the latest version may help resolve any issues you are experiencing.
- Reset IDM settings: If you have recently changed any IDM settings, you may want to try resetting them to the default settings. To do this, go to the “Options” menu in IDM, then select “General.” Click on the “Reset All” button to reset the settings to their default values.
- Check for conflicts with other software: Sometimes, conflicts with other software can cause issues with IDM. Try disabling any other software that may be running in the background, then restart IDM to see if this resolves the issue.
- Reinstall IDM: If none of the above steps have helped, you may want to try uninstalling and reinstalling IDM. This can sometimes help resolve any issues with the software.
If you are still experiencing issues after trying these steps, you may want to contact IDM support for further assistance.
Internet Download Manager (IDM) is a popular download manager software that has been around for over two decades. It is a tool that helps users download files from the internet at a faster speed and with greater efficiency. IDM has become a popular choice for people who want to download large files such as movies, software, games, and other multimedia content from the internet. This article will provide an overview of Internet Download Manager, its features, and benefits.
Overview of Internet Download Manager
Internet Download Manager (IDM) is a software tool that helps users download files from the internet at a faster speed than the regular download speed. The software integrates seamlessly with popular web browsers such as Google Chrome, Mozilla Firefox, Microsoft Edge, and others. IDM divides the files into smaller segments and downloads them simultaneously, which speeds up the download process. IDM is available for Windows operating systems and has a user-friendly interface.
Features of Internet Download Manager
- Faster Download Speeds: IDM uses dynamic file segmentation technology to increase download speeds. It can divide a file into several smaller parts and download them simultaneously, which can improve download speeds by up to five times.
- Resume Downloads: IDM allows users to resume downloads that were interrupted due to a network error or system shutdown. It saves the partial download progress and resumes the download from where it was interrupted, which saves time and bandwidth.
- Schedule Downloads: IDM can schedule downloads at specific times, which is useful for people who have limited internet bandwidth during peak hours. Users can set the download to start at night or during off-peak hours.
- Integration with Web Browsers: IDM integrates seamlessly with popular web browsers such as Google Chrome, Mozilla Firefox, Microsoft Edge, and others. It can automatically detect downloadable content and start the download process.
- Download Categories: IDM allows users to categorize their downloads into different categories such as documents, music, videos, and software. It makes it easy to manage downloaded files and locate them on the user’s computer.
Benefits of Internet Download Manager
- Increased Download Speed: IDM can increase download speeds by up to five times, which saves time and bandwidth.
- Resume Downloads: IDM allows users to resume interrupted downloads, which saves time and bandwidth.
- Schedule Downloads: IDM can schedule downloads at specific times, which is useful for people who have limited internet bandwidth during peak hours.
- Easy to Use: IDM has a user-friendly interface that is easy to use, even for beginners.
- Safe and Secure: IDM is a safe and secure download manager that does not contain any malware or viruses.
Internet Download Manager (IDM) is a powerful download manager tool that can help users download files from the internet at a faster speed and with greater efficiency. It offers a range of features such as faster download speeds, resume downloads, schedule downloads, integration with web browsers, and download categories. IDM is easy to use, safe, and secure. It is a popular choice for people who want to download large files such as movies, software, games, and other multimedia content from the internet.
Internet Download Manager (IDM) is a powerful download manager that can increase download speeds and make the download process more efficient. This article will provide a step-by-step guide on how to use IDM.
Step 1: Download and Install IDM
The first step is to download and install IDM on your computer. You can download IDM from the official website or from third-party download sites. Once you have downloaded the setup file, double-click it to start the installation process. Follow the on-screen instructions to complete the installation process.
Step 2: Configure IDM Settings
After installing IDM, you need to configure the settings to make sure it works optimally. Click on the “Options” button in the IDM window to access the settings. You can configure the settings for the download location, download speed, file types, and other options.
Step 3: Start a Download
To start a download, open your web browser and navigate to the file you want to download. IDM will automatically detect the downloadable content and display a download button on the screen. Click on the download button to start the download.
Step 4: Monitor the Download Progress
You can monitor the download progress by clicking on the “Downloads” tab in the IDM window. The tab will display the list of downloads, their status, and the remaining time. You can also pause, resume, or cancel a download from this tab.
Step 5: Schedule Downloads
IDM allows you to schedule downloads at specific times. To schedule a download, click on the “Add URL” button in the IDM window. Enter the download URL and click on the “Schedule” button. Select the date and time you want the download to start and click on the “OK” button.
Step 6: Use IDM to Download
IDM can also be used to download YouTube videos. Open your web browser and navigate to the YouTube video you want to download. Play the video and IDM will automatically detect the video and display a download button. Click on the download button to start the download.
Step 7: Use IDM to Download Torrents
IDM can also be used to download torrents. To download a torrent file using IDM, you need to use a torrent client that supports IDM integration. Examples of such clients include BitComet, uTorrent, and Vuze. Once you have installed the client, open it and configure the IDM integration settings. You can then download the torrent file using the client, and IDM will take over the download process.
Internet Download Manager (IDM) is a powerful download manager that can increase download speeds and make the download process more efficient. To use IDM, you need to download and install it on your computer, configure the settings, start a download, monitor the download progress, schedule downloads, and use it to download YouTube videos and torrents. With these simple steps, you can make the most of IDM and improve your download experience.
Internet Download Manager (IDM) is a popular download manager software that can help you make money. In this article, we will explore various ways to make money with IDM.
- Affiliate Marketing
One way to make money with IDM is through affiliate marketing. You can become an affiliate marketer for IDM and earn commissions by promoting the software. You can create a blog or a website to promote IDM and share your affiliate links. When someone clicks on your link and purchases IDM, you will earn a commission.
- YouTube Tutorials
Another way to make money with IDM is by creating YouTube tutorials. You can create tutorials on how to use IDM and share them on YouTube. You can monetize your YouTube channel with ads or sponsorships, and also promote IDM in your videos. By doing so, you can earn money from both YouTube and IDM commissions.
- Paid Download Service
You can also create a paid download service using IDM. You can offer premium downloads that are not available elsewhere and charge a fee for each download. By using IDM, you can make the download process faster and more efficient, which can attract more customers.
- Offer IDM Installation Services
If you are good at installing software and troubleshooting computer issues, you can offer IDM installation services to others. You can charge a fee for installing IDM on someone’s computer and configuring it to work optimally. This can be a great way to make money if you have the necessary skills.
- IDM Customization Services
IDM allows for customization of its settings and features. You can offer customization services to others by configuring IDM to their specific needs. You can charge a fee for customizing IDM for someone’s specific download requirements.
Internet Download Manager (IDM) is a versatile software that can help you make money in various ways. You can become an affiliate marketer for IDM, create YouTube tutorials, offer a paid download service, offer IDM installation services, or provide IDM customization services. With these ideas, you can make money with IDM and maximize its potential.
IDM has an automatic update option, and IDM can check for the availability of a new version once per week. Once a new version becomes available, IDM will show a dialog that describes all new features and suggests updating your current version. You may also check for updates manually at any time using “Help→Check for updates…” IDM main menu item.
What’s new in version 6.42 Build 17
(Released: Jul 24, 2024)
- Resolved the problem that caused “403 Forbidden” error. For fixing the problem in all cases, all users are also required to update to 6.42.15 version of “IDM integration module” extension in their browsers
- Fixed a bug that caused Windows Explorer to crash